Abstract of Wardriving
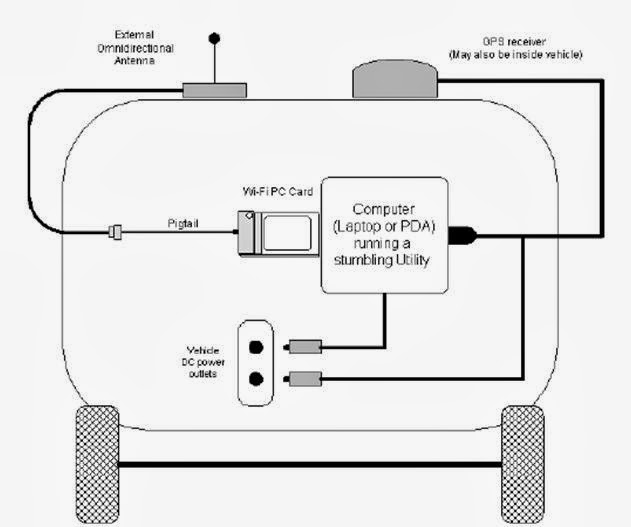
It involves using a car
or truck and a Wi-Fi-equipped computer, such as a laptop or a PDA, to detect
the networks. It was also known as 'WiLDing' (Wireless Lan Driving).Many
wardrivers use GPS devices to measure the location of the network find and log
it on a website. For better range, antennas are built or bought, and vary from
omnidirectional to highly directional. Software for wardriving is freely
available on the Internet, notably, NetStumbler for Windows, Kismet for Linux,
and KisMac for Macintosh.
Wardriving was named
after wardialing because it also involves searching for computer systems with
software that would use a phone modem to dial numbers sequentially and see
which ones were connected to a fax machine or computer, or similar device.
Introduction
WarDriving is an
activity that is misunderstood by many people.This applies to both the general
public, and to the news media that has reported on WarDriving. Because the name
"WarDriving'* has an ominous sound to it, many people associate WarDriving
with a criminal activity WarDriving originated from wardialing, a technique
popularized by a character played by Matthew Broderick in the film WarGames,
and named after that film. Wardialing in this context refers to the practice of
using a computer to dial many phone numbers in the hopes of finding an active
modem.
A WarDriver drives
around an area,often after mapping a route out first, to determine all of the
wireless access points in that area. Once these access points are discovered, a
WarDriver uses a software program or Web site to map the results of his
efforts. Based on these results, a statistical analysis is performed. This
statistical analysis can be of one drive, one area, or a general overview of
all wireless networks. The concept of driving around discovering wireless
networks probably began the day after the first wireless access point was
deployed. However,WarDriving became more well-known when the process was
automated by Peter Shipley, a computer security consultant in Berkeley,
California. During the fall of 2000,Shipley conducted an 18-month survey of
wireless networks in Berkeley, California and reported his results at the
annual DefCon hacker conference in July of 2001.This presentation, designed to
raise awareness of the insecurity of wireless networks that were deployed at
that time, laid the groundwork for the "true" WarDriver.
The truth about WarDriving
The reality of
WarDriving is simple. Computer security professionals, hobbyists, and others
are generally interested in providing information to the public about security
vulnerabilities that are present with "out of the box" configurations
of wireless access points. Wireless access points that can be purchased at a
local electronics or computer store are not geared toward security. They are
designed so that a person with little or no understanding of networking can
purchase a wireless access point, and with little or no outside help, set it up
and begin using it.
Conclusion
The sudden popularity of wireless networks,
combined with a popular misperception that no
additional steps to secure those networks are necessary, has caused a
marked increase in the number of
insecure computer networks that can be accessed without authorization. This
in turn has given rise to the sport of
wardriving detecting and reporting the existence of insecure wireless networks, ostensibly without
actually accessing the network. Wardriving may also involve illegally accessing and monitoring
the networks once so discovered. The sport of
discovering connections to wireless computer networks can be done while
driving in a car or while strolling on
foot with a PDA.
No comments:
Post a Comment